Creating Digital Signature for Project Data
| Note
The package signing feature is supported for PLCnext Technology targets with a firmware version 2025.0 or newer. |
PLCnext Engineer allows you to secure the binary data (programs and sources of the PLCnext Engineer project; applies to non-safety-related and safety-related data) to be written to the target controller by a digital signature. The digital signature ensures the origin, integrity, and security of the data. The signature is checked before the data are loaded into the memory.
The digital signature is created by using the private key of a code signing certificate. The code signing certificate ensures that the data the user is writing to the target controller have not been tampered with or changed since they were signed.
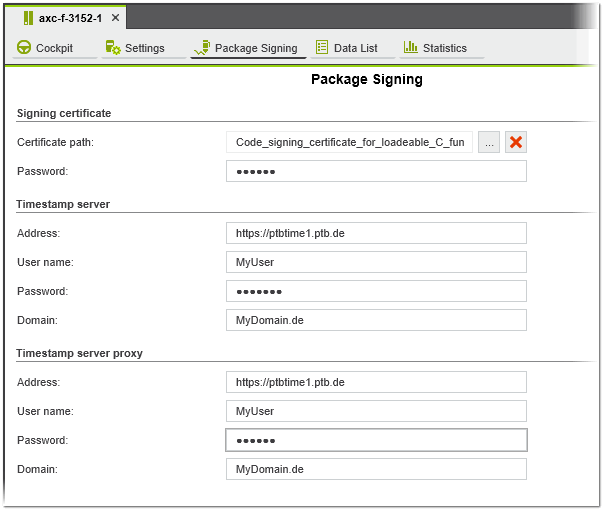
To create a digital signature for securing the data during the write process to the controller, the following information and data must be provided in the 'Package Signing' editor (editor of the controller node):
- Signing certificate (mandatory)Path to the signing certificate container in PKCS12 format (.pkcs12 or .pfx) you want to use to generate the digital signature and the password of the certificate container. The container must include the private key, corresponding public key, and
the certificate chain (trust list).
Signing certificate container and the corresponding password are mandatory for a signed writing of the binary data. - Timestamp server (optional) When generating the digital signature, a timestamp is always added to the signature. By default (no timestamp server is specified), the digital signature will be time stamped from the local computer's time (current UTC date and time). To add a timestamp coming from a timestamp server (trusted third-party service), enter the server address (URI of the timestamp server) and the credentials used for authentication (user name, password, and domain). If no credentials are entered, the default credentials will be used.The timestamp itself is signed with the selected signing certificate and subsequently checked and verified by the firmware on the controller. A corresponding public key must also be contained in the trust list (list of certificates which are trusted). The timestamp ensures that the data were signed at a certain point in time (time of the signature creation) and have not been altered since then. By timestamping the digital signature, the signature of the data is preserved even if the signing certificate has expired.
Note
Timestamping using a timestamp server requires an Internet connection. (No Internet connection is required for the verification on the controller.)Note
When you log in to a service like a timestamp server, the server might need both domain and proxy information (see below) to verify that you are an authorized user and to route your request through the appropriate network. - Timestamp server proxy (optional)Address of the proxy server (e.g., http://proxy.example.com) used for the request and the credentials used for authentication (user name, password, and domain). If not provided, the default web proxy will be used.