Firewalls
Dieses Thema enthält die folgenden Abschnitte:
- General information on firewalls
- Configurable firewall features
- Stateless and stateful firewalls
- Integrated and dedicated firewalls
- Firewall(s) protecting the Demilitarized Zone (DMZ)
- Blacklists and whitelists
General information on firewalls
A firewall is a system component which protects individual computers, IT systems and ICS networks from attacks and data corruption/misuse. Firewalls can prevent or restrict the spread of malware.
The firewall is installed at a suitable system boundary. i.e., zone boundary in our context. It analyzes the inbound and outbound data traffic and detects unauthorized access based on the properties of the network packet. Network packets that are not allowed are blocked by the firewall.
By eliminating all of the communication options that are not technically necessary, many attacks to your network would not even be possible. In addition, industrial integrity monitoring helps you detect and halt the impact of changes and manipulations to Windows-based systems, such as controllers, operator interfaces or PCs, in good time.
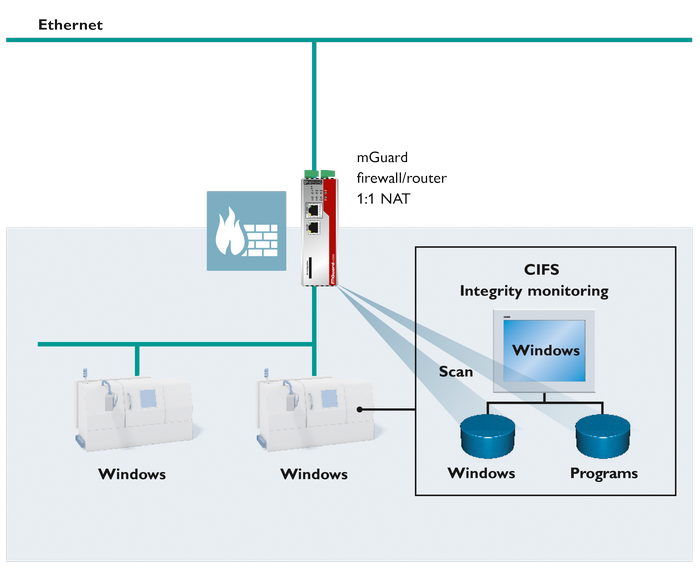
The following figure shows an example with an mGuard firewall/router and 1:1 NAT as well as integrity monitoring.
Configurable firewall features
For configuration purposes, each firewall offers a corresponding user interface where rules and exceptions for blocking and passing must be defined. Such rules are, for example:
| Hinweis
Some of the feature mentioned below are only supported by so-called Next Generation Firewalls (NGFW). |
-
Packet Filtering: Which network packets are allowed to pass? To determine this, the firewall evaluates the IP-related information such as the packet's IP source and destination address and the ports used by the communication connection. Firewalls that support Stateful Packet Inspection also evaluate the condition of the IP connection involved. See section "Stateless and stateful firewalls" for details.If Deep Packet Inspection (DPI) is supported, dynamic packet filtering also takes place. The information contained in the data packets is read, analyzed and evaluated. The firewall recognizes the type of user data (text, graphics, audio, video). In this way, different types of malware can be detected, which can prevent DoS attacks, for example. In addition, unwanted data traffic (e.g. Spam) can be detected and filtered out (reduction of data traffic load).
Hinweis
DPI works only for plain (unencrypted) traffic.Hinweis
Since the content of the data packets is read, compliance with applicable data protection guidelines must be ensured when using DPI. - Network Access Translation: A NAT function hides the resources behind the firewall from the public network thus making them unavailable from external. See topic "Network Access Translation" for details.
-
Proxy: If a firewall supports the proxy function, it can be parameterized to forward requests to the external network coming from inside the protected zone. This way, the firewall appears as source for outbound data packages. A proxy handles vicariously the entire communication and it is able to analyze and block (if required) transmitted content. This way, participants inside the protected zone can be prevented from loading unauthorized content outside. Configurable content filters may enhance this functionality.
The most common type of proxy is a HTTP proxy for web traffic.Hinweis
In addition, the proxy may be able to provide the same services for inbound traffic. - URL Filtering: URL filters are typical functions of HTTP/web proxies. By defining a list of URLs of forbidden websites or services (black list), the access to potentially harmful data sources can be blocked for participants inside the protected zone. In the same way, a white list can define permitted sites that have been verified as non-hazardous. See section "Black/white lists" for details.
- Antivirus and Malware Inspection: All system components for which anti-malware software is available should be protected with a modern (next generation) malware prevention tool. For details, refer to the chapter "Antivirus and Malware Inspection".
Stateless and stateful firewalls
Firewalls that support Stateful Packet Inspection are referred to as stateful firewalls. The difference between stateless and stateful firewalls is described in the following.
A "classical" stateless firewall inspects ingoing network packages based on filtering rules which have been defined for inbound and outbound traffic by an administrator. For that purpose, it inspects, for example, only the source and destination IP address of network packets. Since the permitted data traffic must be configured for both transmission directions, it is not possible to determine which of the communication partners (peers) initiated the connection. As this is static information, such a firewall is referred to as stateless firewall. If an inbound data packet matches the conditions for passing, the stateless firewall guides it into the network (according to defined rules). Otherwise, i.e, if a packet cannot be identified, it is rejected.
In contrast, a stateful firewall controls the network traffic on a more comprehensive basis and is therefore more restrictive. For that purpose, it inspects the entire state of the existing network connections by considering state information from past communications.
For example, a stateful firewall also considers the connection state by analyzing the data transfer on the transport layer (which is the 4th layer of the OSI model). This way, it inspects the complete context of the network and decides dynamically on each current communication attempt.
- Addressing anomalies (IP source and destination address identical, broadcast/multicast source address, etc.)
- Packet anomalies (incorrect IP address, bad IP header checksum, incorrect IP options, etc.),
- Fragmentation anomalies (IP length errors, etc.),
- Protocol anomalies (e.g., incorrect TCP flags and TCP sequence numbers)
A stateful firewall works according to the handshake principle and takes the times into account at which data packets are expected and received (timeouts are possible).
Any permitted connections (packets) are entered in a dynamic state table allowing connection tracking. Since NAT gateways must assign port numbers dynamically, they require state tables and are therefore always stateful.
Conclusion: Stateful firewalls provide a higher level of protection than stateless firewalls. Therefore, they are the current state of the art.
Stateless firewalls are hardly available on the market anymore.
However, they require a higher hardware performance due to their operating principle. This makes them more vulnerable to DDoS attacks.
Integrated and dedicated firewalls
A firewall can be installed on a separate hardware unit (which is then referred to as dedicated firewall) or it can be a software component which is installed within the unit to be protected (integrated firewall).
Figure 1: Integrated firewall
An integrated firewall, as shown in Figure 1, offers cost advantages but is more vulnerable to attacks, depending on the quality of the main system implementation. If many different components with integrated firewalls are to be used, all possible variants must be administered and maintained. If the main system is successfully attacked, the firewall can be infiltrated as well.
Figure 2: Dedicated firewall
A dedicated firewall as a stand-alone device (Figure 2) requires a targeted investment but allows selection independent of the other automation components. In addition, there are the following advantages of dedicated firewalls over integrated firewalls:- Central administration is possible.
- Component is more robust against vulnerabilities in other automation components.
- Patches and updates are possible without affecting the function of the overall system.
- In the event of a network overload, the firewall can absorb the load thus protecting the automation components behind it.
Firewall(s) protecting the Demilitarized Zone (DMZ)
The DMZ is a buffer zone between the ICS and other networks. This other network can be a public one or, for example, an internal office network. See section "Special zone: DMZ" for details.
A DMZ can be protected by one or two firewalls:- When implementing a single firewall (e.g., for cost reasons), this firewall should at least provide three network ports for connecting the external network, the DMZ and the ICS-internal network.
- When implementing two firewalls, one could be located between the external network and the DMZ, another firewall between the DMZ and other ICS-zones.
The DMZ firewall(s) must control the data flow as follows:
- Accesses from external networks (Internet) must only be possible to components (authentication servers, application gateway, etc.) in the DMZ. No direct access from external networks to resources within the ICS network is allowed.
- Accesses from the ICS-internal network must not directly access resources located in external networks. Instead, an intermediate point such as a proxy server in the DMZ must be interposed.
- Data packages must only leave the DMZ (in direction internal network and Internet) if they are authorized accordingly.
Blacklists and whitelists
Blacklists and whitelists pursue opposing strategies. Therefore, usually only one of the two lists is used, but not both together.- A whitelist is a "positive list", or in other words a list of all exceptions to a general prohibition. This means that no connections are allowed through the appropriately configured firewall except those explicitly listed on the whitelist. A prerequisite for the use of a whitelist is that all permitted connections must be known. The list must be updated for each new communication connection that is classified trustworthy.
- A blacklist is a "negative list", i.e. a list of all exceptions to a blanket permission. It contains all connections that are considered untrustworthy and should therefore be prevented. A prerequisite (and a disadvantage) for using a blacklist is that all prohibited connections must be known.
| Weitere Infos
For detailed information on the management settings for the firewall used refer to the respective user manual or the online help of the corresponding configuration software. |