IEC 62443 Compliance
The IEC 62443 standard defines functional requirements regarding the security of Industrial Control and Automation Systems (IACS) regarding:
- Identification and authentication control
- Use control
- System integrity
- Data confidentiality
- Restricted data flow
- Timely response to event
- Resource availability
From these functional requirements, application-specific system requirements can be derived and implemented accordingly.
Furthermore, the IEC 62443 standard defines three different roles. Depending on your role, different security-related requirements arise in order to become certified according to the IEC 62443 standard.- Role 1: Manufacturer or Product Supplier - with regard to PLCnext Technology controllers and PLCnext Engineer, this is Phoenix Contact.
- Role 2: System Integrator
As a system integrator, you are responsible for the standard-compliant integration and commissioning of the PLCnext Technology controller and the connected devices involved into an automation solution. - Role 3: Operator or Application/System Owner
As an application owner/operator, you are responsible for implementing and following the standard-compliant policies, capabilities, and procedures that secure the operation and maintenance of the automation solution on-site.
Consider the following security-related measures to protect PLCnext Engineer, the data and solutions created with it as well as your PLCnext Technology application.
| Security Stage | Description |
|---|---|
| Protection of the PC on which PLCnext Engineer runs | Implementation of a suitable user
authentication on the Windows PC must ensure that the user is known and authorized to use PLCnext Engineer.
|
| Integrity check of the downloaded PLCnext Engineer setup file | After downloading the setup and prior to the installation, you
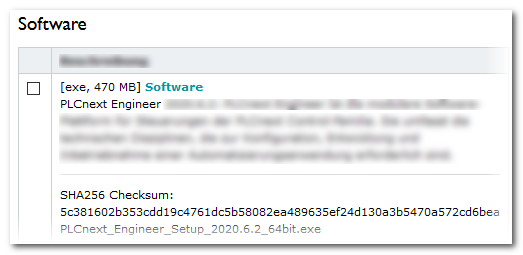
should verify that the downloaded PLCnext Engineer setup file has not been corrupted/tampered.For that purpose, compare the SHA256 checksum which is noted for each software in the Phoenix Contact Download Center with the checksum of the downloaded file.
 Example
After downloading the setup file, use a suitable tool to calculate a SHA256 checksum over the downloaded file. If the calculated SHA256 checksum is identical with the checksum listed in the Phoenix Contact Download Center, the setup file can be executed. Example
After downloading the setup file, use a suitable tool to calculate a SHA256 checksum over the downloaded file. If the calculated SHA256 checksum is identical with the checksum listed in the Phoenix Contact Download Center, the setup file can be executed.
 Example Example
|
| Integrity check of the PLCnext Engineer installation | Primarily, use a standard Windows tool to verify that the PLCnext Engineer installation is not tampered/corrupted.Alternatively, the ChecksumCalculator tool is provided by Phoenix Contact:When installing PLCnext Engineer, checksums are calculated over the installation. By verifying these checksums, manipulations and data corruption can be detected. For that purpose, the ChecksumCalculator can be executed regularly to monitor the integrity of the PLCnext Engineer installation. See topic "Security Guideline for PLCnext Engineer" for further information. |
| Protection of project data | PLCnext Engineer implements features for project data protection:
|
| Protection of data transmission between PLCnext Engineer and PLCnext Technology controller | PLCnext Engineer implements features for securing the data connections between the engineering software and the controller firmware: only authorized users can communicate with the controller via a secured connection.
|
| Protection of data transmission between the integrated OPC UA server and its clients | PLCnext Engineer implements features for securing the data connections between the OPC UA server integrated in the PLCnext Technology controller and the connected OPC UA clients.Refer to the topic " Network Security: OPC UA Server Security Settings " for details. |
| Protection of data transferred via HMI and WBM (Web Based Management). | The HMI data of your project are stored on the controller in the internal Web Server. Using a web browser as client, these data and the variables values (stored in the controller's GDS Global Data Space) are accessed via the Internet. When opening the HMI pages, this data transmission is secured via certificates and default web technologies. Therefore, a login with a user name and password is implemented. The following applies:
|