'Server Settings' Editor (OPC UA)
The following information refers to a specific, typical device type. Your screen may differ.
This help topic describes the 'Server Settings' editor of the 'OPC UA' PLANT node. Here, you can configure basic and security settings and, if required, a discovery server. Furthermore, you can specify the access to the (Linux) file system on the PLCnext Technology controller by OPC UA clients.
Further Info
Details and procedures can be found in the help chapter "OPC UA server". |
On the left side on the 'Server Settings' page, several editor categories can be selected. These are described below in detail.
This topic contains the following sections:
'All'
After selecting the 'All' category, the settings that are available in each category are visible on one page.
'Basic settings'
 Click here to see the parameter descriptions
Click here to see the parameter descriptions
| Section | Parameter | Description |
| Endpoint | DNS Name / IP Address | Name of the controller in the Domain Name System (DNS) where the OPC UA server is installed as embedded application. A name server can uniquely identify the server using this name by mapping the DNS name to the controller's IP address. |
| Information Model | Visibility of variables | Specifies the implementation of the information model and therefore the visibility of data for OPC UA clients.Using these options, you can define the data structure the OPC UA server will provide to its clients.'IN/OUT-Port visibility'
- 'all': all ports and variables contained in the application's GDS (Global Data Space) are visible and accessible for OPC UA clients.
- 'marked': only ports and variables for which the 'OPC' property is selected in the variables declaration table are visible and accessible for OPC UA clients. Using this option and selecting the required variables in the declaration table, the load of the OPC UA server as well as the communication traffic can be reduced.
- 'none': clients cannot subscribe any port or variable via the OPC UA server. The entire 'PLCnext' node is excluded from the data information model.The Device Information (DI, according to the OPC UA standard) remains visible for clients. This includes controller information such as hardware and software revision numbers, serial number, manufacturer name, model specification, etc.
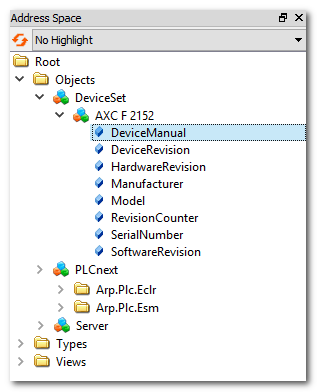
 Example Example
Information model visible in an example client. The OPC UA server is embedded in the PLCnext Technology controller AXC F 2152. The setting 'all' results in the following data structure:
- The 'PLCnext' node contains the ports and variables provided for the OPC UA clients.
- The 'AXC F 2152' node contains the OPC UA standard Device Information
|
| Specification | Enable Specification | Only available for PLCnext Technology controllers with a firmware version 2023.6 or newer.Enables the configuration of the maximum number of concurrent OPC UA client sessions for the OPC UA server. Possible values:
- 'No' (default) - The default value specified for the maximum number of concurrent OPC UA client sessions in the firmware of the controller is used for the OPC UA server.
- 'Yes' - The value entered for the maximum number of concurrent OPC UA client sessions (see the following parameter group) is used for the OPC UA server.
|
| Maximum no. of sessions | Enable maximum no. of sessions | Only available for PLCnext Technology controllers with a firmware version 2023.6 or newer.Maximum number of concurrent OPC UA client sessions the OPC UA server will allow. (The parameter group is only available if the parameter 'Enable Specification' is set to 'Yes', see above).Set 'Enable maximum no. of sessions' to 'Yes' and enter the maximum number of concurrent OPC UA client sessions in the input field below.
With 'Enable maximum no. of sessions' set to 'No', the default value specified in the firmware of the controller is used.
Note
The default value and possible value range of concurrent OPC UA client sessions depends on the PLC type used. |
|
| Subscription Settings | Subscription Kind | Kind of PLCnext subscription that is used by the OPC UA server.Possible values:
- 'Direct Read': With this setting, values are recorded independently of the ESM tasks defined in your controller application. Instead, values are read directly from the respective variables as soon as the responsible firmware function is called. This way, data subscriptions from different ESM task cycles are possible.
This setting may be useful for the asynchronous subscription of non-time-critical data. It has no influence on the real-time behavior.'Direct Read' is the default setting for new projects and after the replacement of an older controller by a controller with firmware version 2021.0 LTS or newer.
- 'High Performance': In this mode, simultaneous reading and writing of data is possible. Each access takes place ESM-task-synchronously. This subscription type consumes the least memory. It actually has impact on the real-time behavior but less than the 'Real Time' mode.
This mode is suitable for the most data acquisition scenarios.
- 'Real Time': In this mode, simultaneous reading and writing of data is made with minimum access times. Therefore, it enables the fastest data access of all three modes but requires the most memory. Subscription is made task-synchronously.
This mode is suitable for subscribing variables in very fast tasks. However, it influences the real-time behavior even more than in 'High Performance' mode.
|
'Security'
 Click here to see the parameter descriptions
Click here to see the parameter descriptions
| Parameter | Description |
| Certificate | Configures the certificate management on the OPC UA server.
- 'File on controller': a certificate file (including a private key) is stored in the IdentityStore on the controller device. This can be a CA-signed or a self-signed certificate (see term definitions at the end of this topic). The location on the controller is fixed and cannot be modified. The transfer of the certificate into the controller's IdentityStore can be done via the Web Based Management (WBM) interface of the controller or using the tool SCP Secure Copy (the transfer is not possible using PLCnext Engineer). Refer to the controller manual of your PLCnext Technology device for details. Refer to the table row 'TrustStores' below for an explanation of the term "IdentityStore".
- 'Self-signed by controller': the server generates and uses the self-signed certificate, generated by the server and signed with its own private key.
Using the self-signed certificate causes greater efforts when establishing a network with many application instances because the certificate must be distributed manually to the involved instances.After selecting 'Self-signed by controller', the 'Subject' options become visible with which you specify subject(s) of the certificate. Modifying these subject settings result in a newly generated self-signed certificate after the next project download. Refer to the table row "Type of subject" below for details.
- 'Provided by OPC UA GDS': The OPC UA server embedded in the PLCnext Technology device is ready to be automatically provided with certificates according to the Certificate Push Management defined by the OPC UA standard (V 1.04, Part 12). This includes the initial certificates as well as all follow-up certificates (updates).The certificates are expected to be automatically provided by a Global Discovery Server (GDS) which implements the push mechanism. The Global Discovery Server is expected to connect to the OPC UA server in the PLCnext Technology device as a "special" OPC UA client.The Global Discovery Server is not part of PLCnext Engineer. Any suitable tool customary on the market can be used. It must be configured accordingly, in order to supply the OPC UA server on the PLCnext Technology device as well as all OPC UA clients (i.e., all relevant devices within your network/security domain) with certificates. Note that the Global Discovery Server can also be located in a different security domain (subnetwork).After having selected 'Provided by OPC UA GDS', you have to define the names for the TrustStore and the IdentityStore of the OPC UA server. The names are freely definable. You can see and inspect the content of these stores at the Web Based Management (WBM) of the controller. The OPC UA server uses them to store data there which it received from the Global Discovery Server (GDS). Into the named IdentityStore it stores the certificate and key which it is instructed by the GDS to authenticate itself against clients. Into the TrustStore it stores trusted and issuer certificates as it receives them from the GDS to verify client certificates with.After selecting 'Provided by OPC UA GDS', the 'Subject' options become also visible with which you specify subject(s) of the certificate. Depending on the Global Discovery Server involved, these subject settings can be integrated in the certificates that will be delivered to the OPC UA server. Refer to the table row "Type of subject" below for details.
|
| Trust Stores | These fields are only visible if 'Server certificate' is set to 'Provided by OPC UA GDS' (see row above).You have to define the names of the TrustStore and the Identity Store which the OPC UA server shall use to store data it receives from the Global Discovery Server (GDS). Enter the freely definable names into the text fields. You can inspect the current content of these stores via the Web Based Management (WBM) interface of the PLCnext Technology device.
For both the TrustStore and the IdentityStore, the following applies:
- The contained data are stored in the PLCnext Technology file system and can optionally be protected by hardware measures. By default, manufacturer-defined TrustStores and IdentityStores can be implemented.
Examples: a default TrustStore which contains data for validating the authenticity of the Proficloud server when establishing a connection to the Proficloud, or an IdentityStore for the authentication at the HTTPS server or the Remoting server of the device.
- TrustStores and IdentityStores on the PLCnext Technology device can be explored via the Web Based Management (WBM) interface.
- In the current implementation, three TrustStores and three IdentityStores are ready for use by the OPC UA server. The OPC UA server currently supports one TrustStore and one IdentityStore at a time. Which one is used depends on the OPC UA server configuration.IdentityStores:
- One IdentityStore with fixed name for the self-signed certificate. This store is used when selecting the configuration option 'Self-signed by controller'.
- One IdentityStore with fixed name for the certificate file. This store is used when selecting the configuration option 'File on controller'.
- One IdentityStore with a name defined via PLCnext Engineer for the certificate pushed by the GDS.
This store is used when selecting the configuration option 'Provided by OPC UA GDS'.
TrustStores:
- One TrustStore with fixed name for use with the certificate file. This store is used when selecting the configuration option 'File on controller' or 'Self-signed by controller'.
- One TrustStore with a name defined via PLCnext Engineer for information pushed by the GDS. This store is used when selecting the configuration option 'Provided by OPC UA GDS'. In this case, the following applies: if not yet defined (e.g., by WBM), you can simply create a new TrustStore or IdentityStore by typing any name into the inputs fields. This way, a corresponding store with this name will be created on the device when the OPC UA server executes the project. Once created, the store will still be empty but listed in the WBM.
Note
As long as the TrustStore is empty, the OPC UA server trusts all clients. |
- The content of both the TrustStore and the IdentityStore can be modified via the WBM interface. This way, you can manually "prefill" the TrustStore in order to enable the OPC UA server to trust the Global Discovery Server which will provide the OPC UA server with further certificates. You can furthermore prefill the IdentityStore with a server certificate in order to enable the server to authenticate itself as trusted member of your security domain, for example, at the Global Discovery Server.
- Configure the Global Discovery Server involved accordingly to trust the OPC UA server (in order to establish a connection between OPC UA server and GDS). Then set up the GDS in a way that it cyclically writes the required security data into the TrustStore and the IdentityStore of the OPC UA server.
Note
The OPC UA standard uses different terms. The standard mentions a TrustList the content of which is very similar to the content of a TrustStore of the PLCnext Technology device. The standard specifies a CertificateGroup which is very similar to the information within an IdentityStore of the PLCnext Technology device. |
|
| Type of subject | These fields are only visible if 'Server certificate' is set to 'Self-signed by controller' or 'Provided by OPC UA GDS'.
Note
In case of 'Provided by OPC UA GDS' it depends on the implementation of the Global Discovery Server involved whether the subject settings made here are considered or not. |
A subject specifies the owner of a certificate. A subject can be accompanied by alternative names. Within certificates according to the X.509 standard these alternative names are recorded within a so-called "subjAltName"-Extension within the certificate.
Using these input fields, you can specify alternative names the OPC UA server shall include in the self-signed certificate it generates or in the certificate signing request it generates for a Global Discovery Server.
You can specify up to five alternative names for the subject. Each alternative name shall describe a DNS name or IP address the OPC UA server is reachable at. The OPC UA server automatically also includes the DNS name specified in the basic settings as an alternative name regardless of the settings here.
This way, you can enable up to four communication paths (provided that this is supported by your network architecture, for example, using a router, existing port forwarding (firewall in router to OPC UA server) and implemented local DynDNS). When establishing the connection, OPC UA clients verify whether the address (DNS name or IP address) from the URL they wanted to connect to is contained in the server certificate.
If several possibilities exist for connecting the OPC UA server from outside or inside the domain, each possible address part of a URL must be contained in the certificate. Otherwise, the authentication fails.Any specified DNS name or IP address (depending on the selection in 'Type of subject') is written into the self-signed certificate. If 'not set' is selected in a subject field, it is ignored by the server when generating the certificate. When specifying 'not set' for all subjects, no alternative name will be included in the self-signed certificate except for the DNS name from the Basic Settings which is always included.
Note
If clients use short URLs (because they are located in the same domain as the OPC UA server), list these short names here as alternative names. |
|
| Security Policies | Security policies specify a set of algorithms to be used and make specifications about key lengths. In accordance with the OPC UA specification, the available algorithms are listed and can be selected here.The selection defines the encryption algorithm(s) (Cipher Suite), the OPC UA server offers to its clients. The encryption algorithm is applied to and secures the data transfer between OPC UA server and client.Select 'Yes' in the relating drop-down list to make the respective algorithm available for clients. If set to 'No', the encryption algorithm cannot be selected in the OPC UA client settings. From top to bottom, the encryption and signature strength increases:
- 'Enable Basic 128 RSA15 algorithm'
This Basic 128 RSA15 algorithm is deprecated and is therefore set to 'No' by default. Only use this setting if the OPC UA client does not support a higher encryption.
- 'Enable Basic 256 algorithm'
This Basic 256 algorithm is deprecated and is therefore set to 'No' by default. Only use this setting if the OPC UA client does not support a higher encryption.
- 'Enable Basic 256 SHA256 algorithm'
This Basic 256 SHA256 algorithm is deprecated and is therefore set to 'No' by default. Only use this setting if the OPC UA client does not support a higher encryption.
- 'Enable AES 128 SHA256 RSA OAEP algorithm'
- 'Enable AES 256 SHA256 RSA PSS algorithm'
|
| Application |
- 'Use the trust store for client authentication' (default setting 'Yes')If activated, the TrustStore (TrustList acc. to the OPC UA spec.) and the Certificate Revocation List (CRL) are used for authenticating OPC UA clients that attempt to connect the OPC UA server. As a result, only clients whose certificate is stored in the TrustStore can connect. Both the TrustStore and the CRL can be viewed and edited via the controller's WBM.
A description of the TrustStore can be found further up in this table. More information on the CRL is contained in the topic "Security terms and background information" (see link above this table).It is recommended to keep the default setting. If set to 'No', the TrustStore and the Certificate Revocation List will not be applied.
- 'Check application URI against client certificate' (default setting 'Yes')If activated, the OPC UA server verifies the ApplicationURI contained in the ApplicationDescription by comparing it with the SubjectAlternativeName.URI in the client certificate. Both URIs are passed from the OPC UA client to the server when the connection is initiated.It is recommended to keep the default setting. If set to 'No', differences between the ApplicationURI from the ApplicationDescription and the URI contained in the client certificate are ignored by the OPC UA server.
|
'Discovery server'
 Click here to see the parameter descriptions
Click here to see the parameter descriptions
| Parameter | Description |
| Discovery registration |
- 'disabled': the OPC UA server does not register at any discovery server.
- 'enabled': by registering the OPC UA server at the specified discovery server (see next entries), the server can be found as endpoint by clients.
|
| Interval | This field is only visible if 'Discovery registration = enabled'.Specification of the time interval after which the OPC UA server has to register cyclically at the discovery server (alive signalization). If the interval elapses without a new registration of the OPC UA server, the OPC UA server is removed from the server list of the discovery server.
The value to be entered depends on the interval value specified for the discovery server. |
| Server url | This field is only visible if 'Discovery registration = enabled'.Replace the pre-configured sample URL opc.tcp://discovery.example.com:4840 accordingly. |
'File system'
 Click here to see the parameter descriptions
Click here to see the parameter descriptions
| Section | Parameter | Description |
| File system | OPC UA file transfer | Sets whether folders and files of the controller file system will be made visible (published) to OPC UA clients in the OPC UA information model.
- 'Disabled' - No folder/file is published.
- 'Enabled' - the settings for specifying the folders to be published become visible.
|
| Show PLCnext Engineer project folderThis field is only visible, if 'OPC UA file transfer' = 'Enabled'. | Makes the directory visible in which the automation project is stored on the controller. |
| Show log files folderThis field is only visible, if 'OPC UA file transfer' = 'Enabled'. | Publishes the directory containing controller log files. |
Published folder x
with x = 1 to 10 | These fields are only visible, if 'OPC UA file transfer' = 'Enabled'.Enable | 'Yes' makes further options visible. |
| Folder | Name of the folder to be published. The symbolic name you enter here, will be represented in the OPC UA information model which can be browsed by clients. (See section "Representation of the controller file system..." below.)
Note
The folders you enter here must already exist on the controller. It is not possible to create new folders by entering a new name. |
|
| Path | Path to the folder. It must consist of the full physical directory path in the controller file system. The entered path is mapped to the 'Folder' name you have entered above.
Note
The folders you enter here must already exist on the controller. It is not possible to create new folders by entering a new name. |
|
| Filter | Optionally, you can define a filter string to hide particular objects in this directory to clients. With the filter setting '*', all folders and files are visible for OPC UA clients and it is possible to create new folders and files.
A particular character combination as filter strings hides all folders which do not contain exactly this combination in its name. Consequently, the files contained in such folders are hidden, too.
The * placeholder combined with a file extension hides all other file types than the specified one. Example: '*.config' shows only config files. |
'Reverse connect'
 Click here to see the parameter descriptions
Click here to see the parameter descriptions
| Section | Parameter | Description |
| Reverse connect | Reverse connect | Sets whether are reverse connection establishment initiated by the clients are allowed.
- 'Disabled' - reverse connect is not allowed.
- 'Enabled' - the settings for specifying client URLs become visible.
|
URLx
with x = 1 to 5 | These fields are only visible, if 'Reverse connect' = 'Enabled'.Enable | 'Yes' makes further options visible. |
| Client URL | URL of the client which has explicit permission to establish the client-sever-connection. |
 Click here to see the parameter descriptions
Click here to see the parameter descriptions
 Example
Example
 Click here to see the parameter descriptions
Click here to see the parameter descriptions
 Click here to see the parameter descriptions
Click here to see the parameter descriptions
 Click here to see the parameter descriptions
Click here to see the parameter descriptions
 Click here to see the parameter descriptions
Click here to see the parameter descriptions
