Security Guideline for PLCnext Engineer
This guideline provides instructions on how to securely handle the PLCnext Engineer software and your solutions/data created with/by the tool.
This topic contains the following sections:
- General measures for PC-based software to reduce the risk of tampering
- Integrity verification of the downloaded setup file
- Running PLCnext Engineer with administrator rights
- Protection of project data on the hard disk and during transfer
- Protect project data by using a Version Control System
- Installation check / tamper detection (administrator information)
- Close projects opened from a removable/network storage after use
- Security-related particularities regarding the Application Control Interface (ACI)
| Further Info
In addition to this topic, also read and observe the information given in the following topics:Also refer to the security-related information in the PLCnext Info Center which provides many information and practical user tips on the PLCnext Technology control platform and PLCnext Engineer |
| Note
Some tool-relating settings are only possible after launching PLCnext Engineer as Windows administrator. This includes, for example, the installation of certificates in PLCnext Engineer or settings, that are included in the tamper detection performed with the ChecksumCalculator tool. Such security-related administrator settings are possible in the 'Options' dialog. |
General measures for PC-based software to reduce the risk of tampering
PLCnext Engineer can manipulate the device or solution. To reduce the risk of manipulation, perform security evaluations regularly.
PC-based hardening and organization measures
Protect any PCs used in automation solution environments against security-relevant manipulations. This can be facilitated, for example, by taking the following measures:
- Boot up your PC regularly, and only from data carriers that are secured against manipulation.
- Set up restrictive access rights for any personnel that absolutely must have authorization.
- Protect your systems against unauthorized access with strong passwords and with rules to ensure that they remain strong.
- Encrypt your project data.
- Deactivate unused services.
- Uninstall any software hat is not used.
- Use a suitable and up-to-date virus/malware detection software.
- Use a firewall to restrict access.
- Use whitelist tools to protect important directories and data against unauthorized changes.
- Activate security-relevant event logging in accordance with the security directive and the legal requirements on data protection.
- Activate the update feature in accordance with the security directive.
- Activate the automatic screen lock function and automatic logout after a specified time.
- Perform backups regularly.
- Only use data and software from approved sources.
- Do not follow any hyperlinks listed that are from unknown sources, such as e-mails.
Use the latest software
- Always use the latest PLCnext Engineer version as well as the latest operating system version on your PC.
- Check for any PLCnext Engineer updates available on the respective product page from Phoenix Contact: www.phoenixcontact.net/product/1046008
- Observe the Change Notes for the respective software version.
- Pay attention to the security advisories published on Phoenix Contact's Product Security Incident Response Team (PSIRT) website regarding any published vulnerabilities.You can also access the PSIRT website via the 'Help' menu in PLCnext Engineer.
Integrity verification of the downloaded setup file
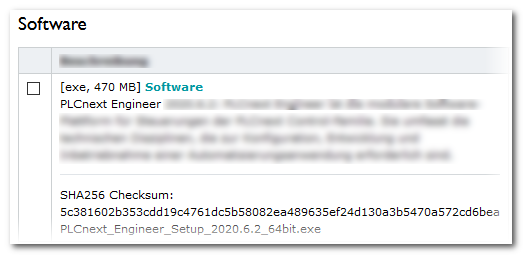
To comply with the IEC 62443 standard, you have to verify that the downloaded PLCnext Engineer setup file has not been corrupted/tampered after downloading the setup and prior to the installation.
For that purpose, compare the SHA256 checksum which is noted for each software in the Phoenix Contact Download Center with the checksum of the downloaded file.
After downloading the setup file, use a suitable tool to calculate a SHA256 checksum over the downloaded file. If the calculated SHA256 checksum is identical with the checksum listed in the Phoenix Contact Download Center, the setup file can be executed.
Running PLCnext Engineer with administrator rights
For some setup operations (for example, the installation of certificates in the trust store), PLCnext Engineer must be executed with administrator rights. While PLCnext Engineer is running with admin rights, installed plugins/add-ons and (also corrupted or manipulated) components may have unrestricted access to your system, data or controller hardware (and therefore possibly to your automation application).
Therefore, make sure that PLCnext Engineer is only started with admin rights if this is absolutely necessary. Exit PLCnext Engineer after you have made the required administrator settings and restart the software with normal user rights.
Protection of project data on the hard disk and during transfer
PLCnext Engineer currently stores plain, i.e., unencrypted project data on the harddisk of your computer. This also applies to project archives and exported libraries. The data is therefore unprotected against tampering and theft.
Use a suitable encryption method:- to protect project data, archives, and exported libraries on your computer.
- to protect the transmission of project data (archives/libraries), for example, by email.
- to authenticate the origin and authorship of transmitted project data with the recipient.
Suitable methods can be provided by encryption and signing tools according to the OpenPGP standard as defined by RFC 4880 (such as PGP, or GnuPG). For encrypting project data on your hard disk, for example, FDE (Full Disk Encryption) tools, such as BitLocker can be used. WinZip archives with password can help protect project files/archives or released libraries.
Furthermore, you can use a version control system with a secured repository to protect your solution data on hard disk/network drive.
Recommendation: Encryption on the entire data transmission path
- Encrypt data on each storage medium (local disks, your network, in the cloud, portable storage media).
- Only transfer encrypted projects parts or libraries, for example, by email.
Suitable Tools (e.g., PGP) enable both the encryption as well as signing of emails: Encryption prevents the unauthorized reading of the mail content while the signature is used to verify the integrity and the authenticity of the mail. - Transferred data should remain encrypted on its entire way from the sender to the receiver. This includes that the sent data are stored encrypted at the target system as well after the transmission.
| Note
Peculiarities for the flat file format: The solution format 'Uncompressed Projects' (*.pcwef) is designed for the source data to be modified directly on the hard disk of your computer. This means that tamper protection by means of hashes and signatures is not possible. Use suitable measures to prevent and detect manipulation or loss of this data. Alternatively you can use the compressed project format for your solution which enables the default data security provided by PLCnext Engineer. To convert the solution, select 'File > Save Project As...' and choose the file type 'Compressed Projects (*.pcwex'). |
Protect project data by using a Version Control System
Solution data on your hard disk or on a network drive could be tampered by external attackers. One possible threat scenario is that an attacker completely replaces the source code of your solution. For example, the current solution data could be replaced by an outdated and (still) buggy version, which could then be written to the controller and put into operation if the intrusion is not detected.
A possible protection measure against this threat of manipulation is the use of a version control system for storing, archiving and versioning the PLCnext Engineer projects.
It should be noted that the VCS used should also be protected against unauthorized access and therefore manipulation. This applies to the communication between the VCS clients (PLCnext Engineer in our case) and the server where the repository is hosted as well as to the repository itself.
Another advantage of a VCS is that it is logged in the repository which PLCnext Engineer user has made which change to the project and when it was made. This change tracking is currently only implemented in PLCnext Engineer for the safety area.
| Further Info
For detailed information, see the topic "Version Management using a VCS". |
Installation check / tamper detection (administrator information)
| Note
By default, access to the PLCnext Engineer installation folder is restricted to Windows admin users. |
You have to continuously check the integrity of the PLCnext Engineer installation. For that purpose, use primarily a standard Windows tool to verify that the PLCnext Engineer installation is not tampered/corrupted.
Alternatively, you can use the ChecksumCalculator tool provided by Phoenix Contact.
| Note
Instead of the ChecksumCalculator tool described here, you can use any other suitable tool. |
The ChecksumCalculator tool provides the possibility to calculate checksums over individual files as well as entire directories (including subfolders, if required). It can be executed for the PLCnext Engineer installation directory thus delivering a checksum over the PLCnext Engineer software installation.
This way, the resulting CRCs consider the following tool settings:- Settings made by Phoenix Contact such as available features and tool characteristics,
- as well as tool settings made by the administrator such as installed customer-specific certificates.
User settings (e.g., made in the 'Options' dialog) are not relevant for this kind of tamper detection as they do not result in any changes in the installation directory of PLCnext Engineer.
ChecksumCalculator is command-line oriented. ChecksumCalculator.exe -? displays help information on the available arguments. Using the -o argument you can write the resulting checksum(s) to a text file you can archive.
Proceed as follows:
| Note
ChecksumCalculator (or any other suitable tool) must only be executed from a trusted data medium. |
- Exclude all files and/or subfolders in the PLCnext Engineer software installation from the checksum calculation which are modified during regular operation. Such files are possibly not accessible by the ChecksumCalculator during operation or no reliable tamper detection is possible as their checksums change frequently. ChecksumCalculator provides arguments for excluding files (-x) or entire folders (-X).
- Execute ChecksumCalculator initially after installing PLCnext Engineer and setting it up.
- Note down the resulting CRCs or archive the text file output by ChecksumCalculator.
- In the following, execute ChecksumCalculator regularly and compare the resulting checksums with the initially calculated and deposited CRCs.
This way, any modification of the PLCnext Engineer installation can be detected by means of a differing checksum.
Close projects opened from a removable/network storage after use
When opening a project from a removable storage medium, such as an USB stick, or from a connected network drive, PLCnext Engineer creates shadow copies. While the project remains open and is edited/stored, changes are made to these shadow copies. When closing the project, these copies are automatically removed.
Shadow copies are stored on your computer under %APPDATA%\Roaming\PHOENIX CONTACT\PLCnext Engineer\${Version}\SHADOW.
Keep in mind that these shadow copies might be compromised, for example, by being modified, replaced, moved, deleted or read/copied by unauthorized access to your computer.
Recommendation: Always close projects opened from such locations after using them in PLCnext Engineer. Then the shadow copies are removed from your PC and no longer represent a potential security risk.
Security-related particularities regarding the Application Control Interface (ACI)
The Application Control Interface (ACI) is an internal interface of PLCnext Engineer which allows remote access to and controlling of the engineering tool. Using the ACI is the only way to operate or run PLCnext Engineer without the user interface.
The ACI has to be enabled/disabled via a checkbox in the 'Options' dialog: Select 'Extras > Options' and select the category 'Administration > Application Control Interface'.
| Note
Enabling/disabling the ACI is only possible after launching PLCnext Engineer with Windows administrator rights and while no project is open. |
Via the ACI, an external application can perform the same operations as via the PLCnext Engineer user interface. With regard to the security of the engineering tool and the controlled automation system, particular vulnerabilities arise from this possibility of remote controlling:
An unauthorized application may control the PLCnext Engineer via ACI. The communication connection is possibly not established between PLCnext Engineer and the ACI client but the engineering tool is connected to an attacker application.Possible damage scenarios can be:
- Manipulation of the ACI communication.
- Engineering projects are loaded, modified or sent to the controller.
- Switching of the controller state.
- Disclosure of confidential data, e.g. user names and passwords, or proprietary project data.
- Nuking of the PLCnext Engineer application.
- Removal of a PLCnext Engineer license.
To prevent an unauthorized communication via the ACI interface, the connection between an ACI client and PLCnext Engineer is secured by means of a cookie which is stored on the engineering PC. This cookie is encrypted (using Windows Data Protection API) and is afterwards specifically bound to the user login. By verifying the cookie on connection establishment, the authenticity of the ACI client and PLCnext Engineer can be verified thus ensuring that the connection is authorized.
Observe the following regarding the ACI concerning cyber security:
- Disable the ACI in the 'Options' dialog whenever it is not used.
- Only users who are authorized to use PLCnext Engineer should have the right to use the ACI client app.
- The ACI client should be identified by authenticating the client user. For that purpose, the client app should support authentication possibilities, e.g. by requesting a login name and password. Furthermore, the PC on which the client app is executed should be protected, e.g. by a login with user name and password.
- The number and type of other applications on the PC on which PLCnext Engineer with enabled ACI is executed should be selected and monitored thoroughly.
- Only users who are authorized to use PLCnext Engineer should have the right to install applications on the PC where PLCnext Engineer with enabled ACI runs.
 Example
Example