360° Security - The Holistic Approach
Comprehensive and sufficient security is not achieved by implementing only (one) technical measures in the system. An adequate security concept must include the technology used, defined processes, and the people involved, i.e., it must specify both technological and organizational measures.
Security must be understood as a mandatory system requirement. Any security-related measures must be integrated with general management structures and organizational processes. Furthermore, they must already be taken into account during the planning phase of processes, plants and execution controls.
Many but not all threats can be defended against with appropriate technical measures, such as, for example, firewalls which filter the communication connections and only allow permitted and known connections. It is, however, important that additional measures are implemented that address personnel, procedures, policies and practices.
A basic assumption of the IEC 62443 is that security mechanisms and processes must be implemented by all three roles (as defined by the standard), rather than by a single actor.
This topic contains the following sections:
Guiding principles
The following important guiding principles apply when developing an Information Security Management System (ISMS):- Security arises from the systemic interaction of the components
- Security can only be economical if measures are taken in the right place. The principle of "equal shares for all" is just as ineffective as "a lot goes a long way".
- To implement technical security measures, the security-related capabilities of the devices used to build automation infrastructures and systems must be utilized as far as possible. To this end, knowledge of these functionalities is necessary as well as the application-specific correct parameterization and configuration.
| Further Info
Please read the chapter "Implementation by Technical and Organizational Means" for details on technical measures. |
Dimensions for a holistic protection
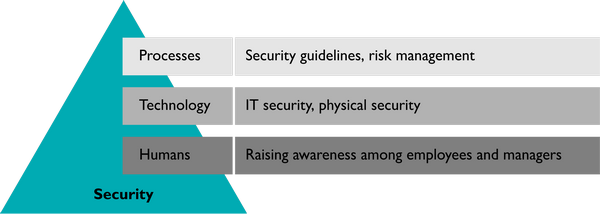
Security can only result, if all of the following three dimensions are considered in a sufficient way. Organizational and technical measures must be defined, implemented and applied/followed.
The figure below illustrates the dimensions of the holistic security measures and the following table explains details.
| Dimension | Offsite consideration (not ICS-specific) | Onsite consideration (specific ICS in operation) |
|---|---|---|
| Process |
| Do the policies and procedures consider and include the necessary security-related aspect regarding the
|
| Technology |
|
|
| People |
|
|
Protection of safety-related data
The protection of safety-related data and therefore the integrity of the safety function is of particular importance.
The manipulation of the safety-related application program may result in:- triggering the safety function without a request having occurred in the application.
- the unavailability of the safety function so that it is no longer triggered when requested.
- the unavailability of the safety function with a simultaneous deliberate causing of the request case.